In an age where cyber threats loom large, the importance of a robust cybersecurity program cannot be overstated. Organizations of all sizes face risks that, if left unaddressed, can lead to severe operational and reputational damage. As attacks evolve and become increasingly sophisticated, a proactive approach to cybersecurity is paramount. The NIST Cybersecurity Framework (CSF) offers a structured approach to strengthen cybersecurity measures. This article serves as a thorough guide on how to bolster your cybersecurity program using the NIST CSF, detailing its core components and practical strategies for implementation.
Grasping the NIST Cybersecurity Framework (CSF)
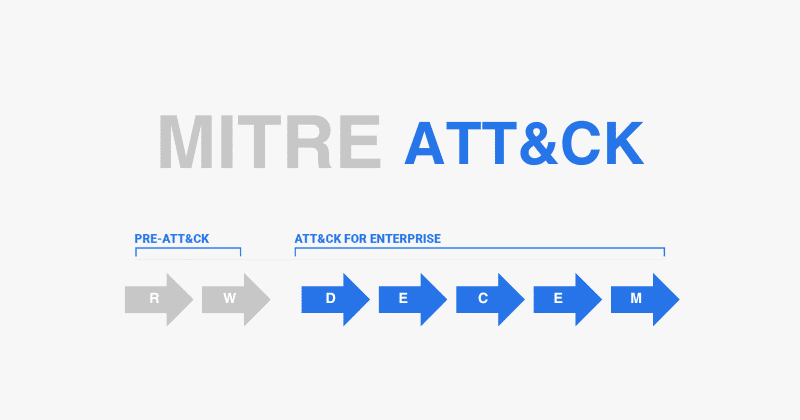
What is the NIST Cybersecurity Framework?
The NIST CSF is a voluntary framework developed to assist organizations in managing and mitigating cybersecurity risk in a straightforward manner. Originating from the National Institute of Standards and Technology, the CSF harmonizes existing standards and best practices while providing a flexible model suitable for diverse organizations across various sectors. Comprising three critical components—Framework Core, Framework Implementation Tiers, and Framework Profile—the CSF allows organizations to customize their cybersecurity practices.
Key Components of the NIST Cybersecurity Framework (CSF)
The Framework Core is essential for risk management, comprising five primary functions: Identify, Protect, Detect, Respond, and Recover. A thorough understanding of these functions is vital:
- Identify: It’s essential to recognize the organization’s risk landscape, including assets, vulnerabilities, and threats. This involves strategic asset management, effective governance, and thorough risk assessments. By identifying these elements, organizations can prioritize and allocate resources effectively to mitigate high-risk areas.
- Protect: This involves implementing appropriate safeguards to ensure the delivery of essential services while minimizing the risk of cybersecurity incidents. Effective protective measures could include access controls, awareness training, data security practices, and technological solutions. Establishing a solid protection layer is vital to prevent the exploitation of identified vulnerabilities.
- Detect: Detection capabilities encompass activities that facilitate the timely identification of cybersecurity events. Employing systems for continuous monitoring, threat intelligence, and anomaly detection can significantly reduce response times, thereby minimizing potential damage.
- Respond: Having an action plan for cybersecurity incidents is critical. This includes developing policies for incident management and communications during cyber events. A well-organized response can drastically shorten recovery times and decrease the overall impact on the organization.
- Recover: The recovery function entails maintaining resilience and having strategies in place to restore capabilities or services after a breach. This includes data recovery plans and stakeholder communication to ensure swift restoration of normal operations.
Benefits of Adopting the NIST CSF
Implementing the NIST CSF offers substantial advantages, profoundly enhancing an organization’s cybersecurity posture:
- Risk Management: The structured framework aids organizations in identifying and addressing vulnerabilities systematically, enabling effective prioritization of cybersecurity controls.
- Improved Communication: NIST CSF fosters enhanced dialogue about cybersecurity practices within the organization and with external stakeholders, clarifying risk-related decisions.
- Heightened Awareness: By focusing on risk identification, NIST CSF promotes a culture of security awareness throughout the organization, making employees conscious of their roles in preserving security.
- Commitment to Improvement: The framework lays the groundwork for continuous evaluation and refinement of cybersecurity practices, enabling organizations to stay ahead of emerging threats.
Implementing the NIST Cybersecurity Framework (CSF) in Your Cybersecurity Program
Establishing Governance
To implement the NIST CSF successfully, organizations must develop a robust governance structure. Clearly defining roles and responsibilities is essential, and appointing a Chief Information Security Officer (CISO) can foster accountability and drive strategic cybersecurity initiatives. Moreover, embedding cybersecurity into corporate governance emphasizes its significance beyond the IT department, recognizing it as integral to overall business health.
Creating a Tailored Implementation Plan
A successful implementation plan should cater to an organization’s unique cybersecurity requirements. Key aspects of the plan should include:
- Objectives: Establish clear, measurable goals, such as reducing vulnerabilities by a predetermined percentage within the next fiscal year.
- Timelines: Define well-structured timelines for the implementation phases, including immediate and long-term actions.
- Resource Allocations: Identify necessary resources—be it personnel, technology, or budget—essential for the successful execution of the framework.
- Measurable Outcomes: Develop key performance indicators (KPIs) to assess progress, with metrics that reflect the effectiveness of the implementation.
Engaging Stakeholders and Cultivating Security Culture
Securing buy-in from stakeholders across departments is crucial for the success of any cybersecurity initiative. Training programs aimed at increasing cybersecurity awareness will empower employees and cultivate a culture of vigilance. Regular communication, workshops, and simulated phishing campaigns can enhance employee engagement, making everyone in the organization aware of their responsibility regarding security.
Continuous Monitoring and Improvement
Implementing Continuous Monitoring
Continuous monitoring should be the bedrock of any cybersecurity strategy. Automated tools that oversee network and system activities are crucial for timely detection of potential threats. Employing intrusion detection systems, Security Information and Event Management (SIEM) software, and continuous vulnerability scanning are effective strategies to maintain visibility over the security landscape.
Conducting Ongoing Risk Assessments
Routine risk assessments are vital for gauging the effectiveness of cybersecurity measures and identifying areas for improvement. Organizations should periodically revisit their risk framework and adjust their practices accordingly, allowing them to stay aligned with their evolving threat landscape. Conducting simulated cyberattacks can unveil weaknesses, propelling further enhancements to defenses.
Framework for Incident Response
An incident response framework is essential to mitigate the impacts of cybersecurity incidents. Regularly revisiting and refining response strategies ensures preparedness. A strong incident response plan will include defined processes for timely identification, containment, eradication of threats, recovery, and lessons learned.
Conclusion
Enhancing your cybersecurity program using the NIST Cybersecurity Framework is a continuous process that necessitates dedication, resources, and collaboration at all organizational levels. By understanding the framework’s core functions, establishing a strong governance structure, and committing to ongoing improvement, organizations can tackle cybersecurity risks with confidence. The steps outlined within this guide represent significant advancements toward a fortified cybersecurity posture, equipping organizations to confront the challenges posed by today’s ever-evolving cyber threat landscape.