In today’s digital Wild West, finance, energy, and tech companies are squarely in the crosshairs of cybercriminals. Think of your IT infrastructure as a modern-day city – if you don’t lock your doors and windows, burglars (hackers) will find a way in. The merging of Information Technology (IT) and Operational Technology (OT) has essentially doubled the size of this “city,” making robust cybersecurity compliance software more vital than ever. But wading through the ocean of available software can feel like trying to find a specific grain of sand. Which solutions provide genuine protection and, crucially, make it easier to navigate the maze of regulations like PCI DSS, HIPAA, DORA, ISO 27001, NERC CIP, and NIST CSF?
This article acts as your compass, providing a comprehensive review of cybersecurity compliance software tailored for the unique needs of finance, energy, and tech companies. It’s designed to guide you towards making smart, informed purchasing decisions, so you can sleep a little easier at night.
The Stakes Are High: Why Cybersecurity Compliance Matters
For organizations in finance, energy, and technology, cybersecurity isn’t just a “nice-to-have”; it’s the bedrock of your business. Neglecting it is like building a house on sand. Consider these compelling reasons:
-
Financial Loss: A single data breach can trigger a financial tsunami, costing millions in damages, fines, and legal battles.
-
Reputational Damage: Think of your reputation as a pristine white shirt. A breach is like a coffee stain that’s hard to remove. Breaches erode customer trust, leading to lost business.
-
Operational Disruption: Cyberattacks can paralyze critical infrastructure – imagine the power grid going down because someone forgot to patch a server! This impacts service delivery and revenue generation.
-
Regulatory Scrutiny: Non-compliance is like ignoring a speeding ticket – it can lead to hefty fines and legal action.
Therefore, investing in effective cybersecurity compliance software is not just a good idea; it’s essential to safeguarding your assets and ensuring your business stays afloat.
Key Cybersecurity Challenges in Finance, Energy, and Tech
While all sectors face the relentless barrage of cyber threats, finance, energy, and tech companies each grapple with their own unique demons:
Finance:
-
Data Security: Imagine trying to protect Fort Knox. The goal is protecting sensitive financial data (credit card numbers, account details) from falling into the wrong hands.
-
Compliance Regulations: Navigating the alphabet soup of regulations like PCI DSS, GLBA, and others can feel like learning a foreign language.
-
Insider Threats: It’s a sad fact, but sometimes the greatest danger comes from within. Mitigating the risk of malicious or negligent actions by employees with access to sensitive information is crucial.
Energy:
-
OT Security: Securing critical infrastructure (power grids, pipelines) is like protecting a city’s water supply. Cyberattacks here can cause widespread chaos and disruption.
-
SCADA Security: Imagine someone gaining control of a city’s traffic lights. That’s the equivalent of a malicious actor controlling SCADA (Supervisory Control and Data Acquisition) systems.
-
Nation-State Threats: Defending against sophisticated attacks launched by state-sponsored groups is like preparing for a battle against a well-funded, highly skilled army.
Technology:
-
Intellectual Property Protection: Safeguarding valuable intellectual property (source code, trade secrets) is like protecting the secret recipe for a million-dollar product.
-
Supply Chain Security: Think of your software as a chain – it’s only as strong as its weakest link. Ensuring the security of software and hardware components from third-party vendors is vital.
-
Evolving Threat Landscape: The threat landscape is like a constantly mutating virus. Adapting to rapidly changing threats and vulnerabilities requires constant vigilance.
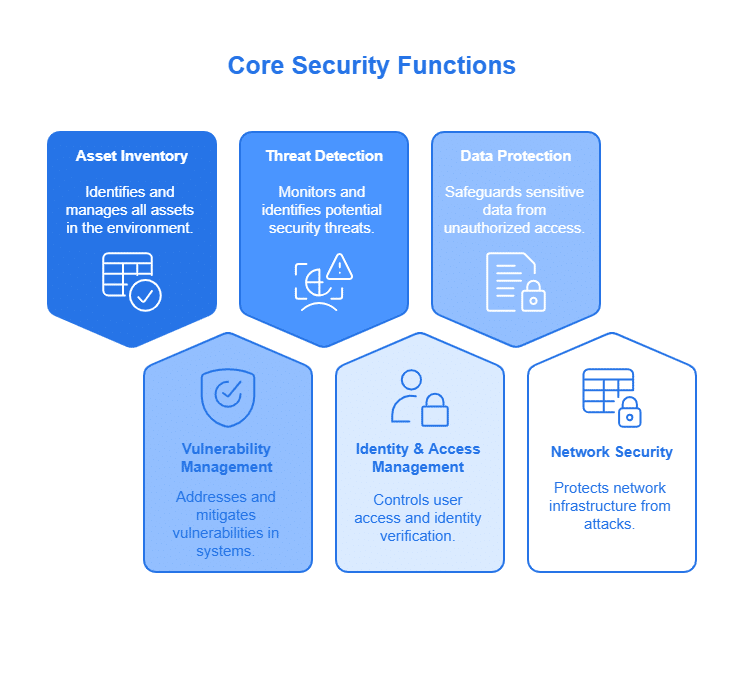
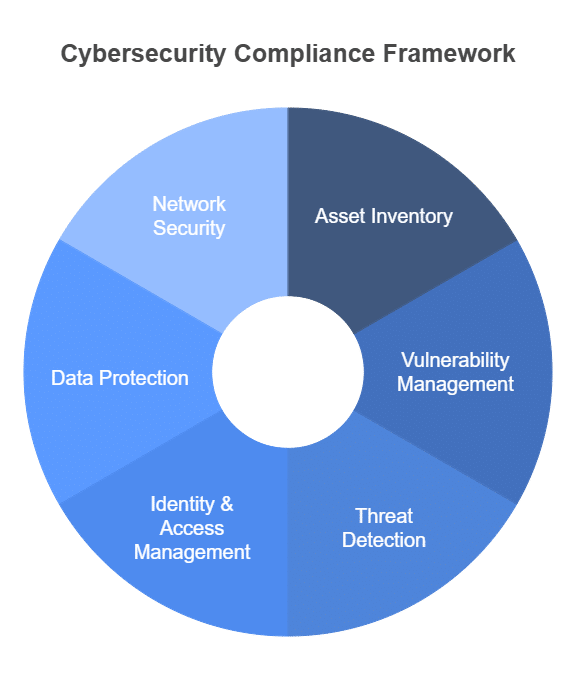
Core Security Functions
To effectively tackle these challenges, cybersecurity compliance software should possess these must-have features:
-
Asset Inventory and Management: You can’t protect what you don’t know you have! Identifying and tracking all hardware, software, and data assets across the organization is the first step. According to NIST SP 800-53, a robust IT asset management program is fundamental to an effective cybersecurity strategy. Think of it as taking inventory of all the valuables in your house.
-
Vulnerability Management: Regularly scanning for and patching vulnerabilities is like fixing cracks in a dam before it bursts. This helps identify and address weaknesses before they can be exploited by cybercriminals.
-
Threat Detection and Logging: Continuous monitoring of network traffic and system logs is like having a security guard patrolling your property 24/7. SIEM (Security Information and Event Management) systems are vital for this.
-
Identity Management and Access Control: Imagine a building with only one key. Implementing strong authentication measures (multi-factor authentication) and enforcing least privilege access is like assigning different keys to different people, ensuring only authorized personnel can access specific areas. Privileged Access Management (PAM) solutions are vital for critical systems.
-
Data Security and DLP: Protecting sensitive data, both when it’s stored and when it’s being transmitted, is like keeping valuables in a safe. Use encryption, access controls, and data loss prevention (DLP) mechanisms.
-
Network Security: Think of your network as a castle. Implementing firewalls, intrusion detection/prevention systems (IDS/IPS), and network segmentation is like building walls, moats, and guard towers to control network access and protect against unauthorized traffic. Network Segmentation is vital to control access.
Compliance and Risk Management
-
Incident Response: Having a well-defined incident response plan is like having a fire escape plan. It allows you to quickly contain, eradicate, and recover from security breaches. Incident Response is key to a sound cybersecurity plan.
-
Risk Assessment and Management: Regularly assessing cybersecurity risks is like assessing land before building a house. The NIST Cybersecurity Framework is a great baseline.
-
Compliance Reporting: Think of these reports as your homework to prove you understand the cybersecurity landscape. Generating reports and documentation is the proof you need to demonstrate compliance with relevant regulations and standards.
-
Software Bill of Materials (SBOM): Think of SBOM as your software’s ingredient list. Generating a list of all components in your software helps you manage supply chain risks.
Top Cybersecurity Software Categories
Here’s a rundown of the key players in the cybersecurity software arena:
-
SIEM (Security Information and Event Management): SIEM systems are like security detectives, gathering and analyzing security logs from various sources to uncover threats and anomalies.
-
Vulnerability Management: These systems act like building inspectors, identifying weaknesses and vulnerabilities in your systems and applications before attackers can exploit them.
-
Endpoint Detection and Response (EDR): EDR solutions are like security guards stationed on every computer and device, providing advanced threat detection, investigation, and response capabilities.
-
Privileged Access Management (PAM): PAM solutions are like high-security vaults, securing and managing privileged accounts to prevent unauthorized access to critical systems.
-
Network Security: These tools are the guardians of your network, securing your network infrastructure with firewalls, intrusion detection/prevention systems, and other security controls.
-
Data Loss Prevention (DLP): DLP solutions are like data guardians, preventing sensitive information from escaping the organization’s control through monitoring, encryption, and access controls.
-
Governance, Risk, and Compliance (GRC): GRC solutions act as compliance automation tool, streamlining processes for Risk Assessment, policy management, and audit reporting.
How to Choose the Right Software for Your Organization
Selecting the right cybersecurity compliance software requires a strategic approach:
-
Assess Your Risk Profile: Think of this as identifying the weak spots in your armor. Determine your unique needs and identify your organization’s most critical assets, potential threats, and vulnerabilities.
-
Define Compliance Requirements: Figure out which rules you need to follow. Determine which regulations and standards your organization must comply with (PCI DSS, HIPAA, DORA, ISO 27001, NERC CIP, NIST CSF).
-
Identify Key Features: Prioritize the features and capabilities that are most important to your organization’s security posture and compliance requirements.
-
Evaluate Vendor Solutions: Research and compare different software vendors, considering factors such as functionality, scalability, ease of use, and cost.
-
Request Demos and Trials: Test drive the software before you buy it. Conduct hands-on testing to ensure it meets your needs and integrates seamlessly with your existing environment.
-
Check Vendor Credentials: Investigate vendor certifications, such as ISO 27001. This offers an added level of assurance.
-
Consider TCO (Total Cost of Ownership): Evaluate the total cost of the software, including licensing fees, implementation costs, training expenses, and ongoing maintenance.
Real-World Examples and Case Studies
Let’s look at some success stories to see how cybersecurity compliance software makes a difference:
-
Financial Institution: Implemented a PAM solution to lock down privileged accounts, dramatically reducing the risk of insider threats and unauthorized access to sensitive financial data. Therefore, compliance requirements were met.
-
Energy Company: Deployed a SIEM system to monitor their OT environment, enabling them to detect and respond to potential cyberattacks on critical infrastructure in real-time. SCADA security improved.
-
Tech Firm: Implemented a supply chain risk management program with a software bill of materials (SBOM), enabling them to identify and mitigate vulnerabilities in third-party software components. As stated in “Cybersecurity Supply Chain Risk Management Strategy Practices for Systems and Organizations” (NIST SP 800-161), strong supplier relationships are critical.
Best Practices for Strengthening Your Cybersecurity Posture
In addition to cybersecurity compliance software, keep these tips in mind:
-
Implement a Security Awareness Training Program: Think of it as teaching everyone how to recognize a phishing email. This will empower employees.
-
Enforce Strong Password Policies: Passwords are your first line of defense.
-
Regularly Patch Systems and Applications: Apply those patches quickly, or it is like leaving your front door unlocked. Enterprise Patch Management is critical. (NIST SP 800-40r4)
-
Implement Network Segmentation: Separate parts of your network to prevent the spread of an attack.
-
Develop and Test Incident Response Plans: Practice makes perfect, so run drills to test how you’ll respond to a breach.
-
Conduct Regular Security Audits: Have third-party experts assess your security posture and identify areas for improvement.
-
Stay Informed: The threat landscape is a moving target. Stay up-to-date.
Future-Proofing Your Security Strategy
The cybersecurity landscape is ever-evolving. Adapt a forward-looking approach to secure your organization:
-
Embrace Automation: Automate tasks to reduce human error.
-
Leverage Threat Intelligence: Know what’s out there.
-
Adopt Zero Trust Principles: Trust no one.
-
Prepare for AI-Powered Attacks: AI is the newest weapon cybercriminals are using. Be prepared.
Solution Focus: Compliance Labs offers advanced threat intelligence and AI-powered security analytics to help organizations stay ahead of the evolving threat landscape.
Conclusion: Proactive Security is the Best Defense
Cybersecurity compliance software is essential for finance, energy, and tech companies seeking to protect their assets and maintain resilience. By assessing your risk profile, defining compliance requirements, and carefully evaluating vendor solutions, you can select the software that best meets your organization’s unique needs. Implement best practices, foster a strong security culture, and partner with an experienced cybersecurity provider. After all, a proactive security strategy is your best defense against today’s ever-evolving cyber threats.
Call to Action:
Ready to strengthen your cybersecurity posture? Contact Compliance Labs today.