In today’s digital era, organizations continually confront an advancing onslaught of cyber threats that challenge their security infrastructures. The fast-paced evolution of cyberattacks, perpetrated by increasingly sophisticated adversaries, necessitates a proactive approach to cybersecurity. To strengthen cybersecurity effectively, organizations must adopt frameworks that provide actionable insights into adversarial tactics.
To effectively counter these threats, it’s imperative for organizations not just to deploy preventative measures but also to deeply understand the tactics and techniques used by cyber criminals. Enter the MITRE ATT&CK framework—a powerful tool designed to equip cybersecurity professionals with the pertinent knowledge and resources essential for navigating and neutralizing cyber threats. This article explores how organizations can leverage ATT&CK for opponent emulation, establishing a foundation to rigorously test and enhance their defensive capabilities.
Harnessing MITRE ATT&CK for Effective Opponent Emulation
Decoding the ATT&CK Framework to Strengthen Cybersecurity
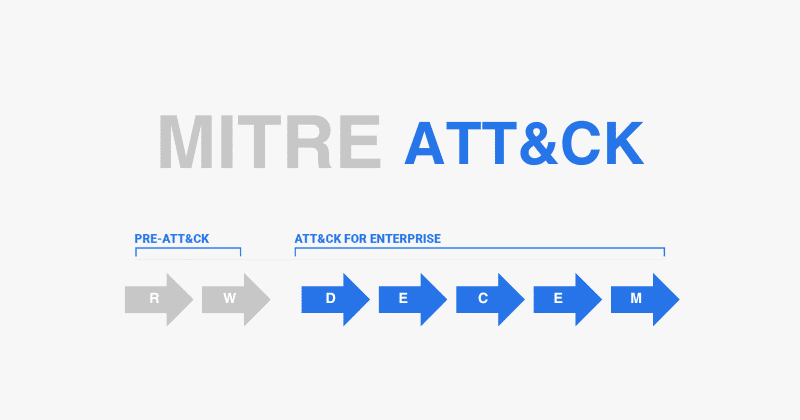
The ATT&CK framework, a brainchild of MITRE, is structured as a matrix that classifies various adversarial tactics and techniques throughout the full spectrum of the attack lifecycle. This spectrum extends from initial access and execution to persistence, privilege escalation, evasion tactics, and impact. The matrix is designed for user-friendliness, facilitating navigation through techniques based on specific threats. Grasping the framework’s layout is vital for effectively aligning adversarial tactics with organizational contexts.
Organizations should consider the ATT&CK framework as a roadmap for identifying adversarial behavior patterns within their operational landscapes. By executing a thorough threat modeling exercise, teams can categorize their data and systems to better align them with applicable ATT&CK tactics. This tactical alignment enhances an organization’s ability to foresee and mitigate unique threats, fostering a more anticipatory cybersecurity posture.
Correlating Techniques with Real-World Threats
The primary strength of the ATT&CK framework is its capacity to correlate theoretical concepts with real-world applications. This correlation empowers organizations to craft realistic attack simulations reflective of recognized adversary behaviors, providing insights into potential vulnerabilities. For instance, an organization in a ransomware-prone sector can concentrate on ATT&CK techniques pertinent to ransomware, including common methods of gaining initial access and techniques employed for lateral movement.
By adopting this directed approach to vulnerability assessments, organizations can bolster their security architecture. They not only discover specific weaknesses but also grasp the potential ramifications of these vulnerabilities being exploited. This deeper contextual understanding plays a pivotal role in risk prioritization, enabling teams to allocate resources strategically to address the most critical areas of concern. By integrating ATT&CK into their assessments, organizations can further strengthen cybersecurity by addressing the highest-priority risks first and deploying resources effectively.
Fortifying Defense Strategies Through Simulation
Simulated Attacks: Testing to Strengthen Cybersecurity Defenses
The regular execution of tests is fundamental to a robust cybersecurity strategy. Rather than merely adhering to compliance standards, active testing scrutinizes existing defenses. Conducting simulated attacks based on ATT&CK tactics enables organizations to measure their defense capabilities against known adversarial techniques, illuminating how well established security measures can withstand potential breaches.
These simulated attacks should include a wide array of scenarios, from basic attacks to advanced persistent threats (APTs). This variety allows security teams to evaluate their detection capabilities, response times, and overall resilience of their infrastructure. Notably, attacks reflecting both internal and external threats are essential, as insider threats frequently employ similar techniques as external adversaries. Overall, these simulations foster a culture of continuous improvement, where organizations fortify their cybersecurity approaches against relentless threats.
Merging Penetration Testing with ATT&CK
Integrating the ATT&CK framework into penetration testing amplifies the effectiveness of such assessments. Traditional penetration testing often identifies vulnerabilities but frequently lacks the strategic context regarding opponent behaviors that ATT&CK can provide. By incorporating ATT&CK, organizations can create penetration tests specifically aligned with their unique environments and relevant threats, giving testers a strategic outline of techniques to investigate.
This integration broadens the effectiveness of penetration testing endeavors. Rather than generically probing for vulnerabilities, teams can prioritize evaluations based on known threats pertinent to their industry and operational framework. By focusing their assessments, organizations can effectively allocate resources and remediate vulnerabilities that adversaries could exploit.
Continuously Enhancing Defenses by Learning from Tests
Assessing Results: Transforming Tests into Advancements
While conducting simulations and tests is of utmost importance, the real value manifests in the evaluation of these outcomes. After executing simulated attacks, organizations must diligently analyze results to determine which defense mechanisms performed effectively and which areas require improvement. This evaluation phase is crucial as it uncovers strengths and weaknesses within existing security measures.
Taking a data-driven approach during evaluations enables organizations to extract actionable insights that can shape ongoing developments in their cybersecurity practices. For example, if a significant proportion of simulated attacks eluded detection, it could signal a pressing need to upgrade security tools or adjust alerting thresholds. Conversely, if certain strategies successfully thwarted attacks, retaining and potentially scaling those measures can further reinforce defenses.
Infusing Insights into Security Policies
The insights gleaned from evaluation processes ought to transition seamlessly into updates for security policies, ensuring that defenses evolve in lockstep with emerging threats. Organizations must focus on integrating feedback from simulated attacks and real-world incidents into their security frameworks to maintain relevance and efficiency. This iterative method not only fortifies existing practices but also equips organizations to confront unanticipated challenges moving forward.
Regularly revising security policies based on emerging tactics within the ATT&CK framework enhances organizational agility and responsiveness, significantly improving resilience against sophisticated adversaries. By nurturing a culture of adaptability, organizations can instill a mindset that embraces change while proactively anticipating future threats.
Securing the Future via ATT&CK
Utilizing the MITRE ATT&CK framework for opponent emulation establishes a robust pathway for organizations striving to assess and enhance their cybersecurity defenses. By thoroughly understanding adversarial techniques, routinely testing defensive capabilities, and continuously refining security policies based on learned lessons, organizations can significantly strengthen their cybersecurity posture.
The proactive approach afforded by the ATT&CK framework not only aids in achieving compliance objectives but also fortifies defenses against the escalating sophistication of cyber threats. Cultivating an ethos of continuous improvement and strategic foresight positions organizations optimally to protect their digital assets against an ever-changing threat landscape.
Emphasizing the ATT&CK framework is not merely an optional endeavor; it is a strategic necessity for organizations committed to effectively mitigating the risks posed by advancing cyber adversaries. By investing in the understanding and practical application of ATT&CK principles, organizations can navigate the complexities of cybersecurity with enhanced confidence, assuring resilience in today’s tumultuous digital landscape.