Navigating PCI DSS v4.0: Mastering Targeted Risk Analyses for Compliance
The Payment Card Industry Data Security Standard (PCI DSS) – it’s not just another compliance hurdle; it’s the cornerstone of protecting sensitive payment data. As someone with over 20 years in cybersecurity, I’ve seen firsthand how critical it is to adapt to the ever-changing threat landscape. And PCI DSS v4.0, with its emphasis on Targeted Risk Analyses (TRAs), represents a significant evolution in safeguarding cardholder information. Think of it like this: if PCI DSS is the blueprint for a secure payment processing system, TRAs are the detailed inspections that ensure every corner of the house is built to withstand the storms of cyberattacks. This article is your guide to mastering TRAs and achieving PCI DSS v4.0 compliance. I’ll share some actionable strategies to protect your cardholder data environment and demonstrate why mastering TRAs is essential to achieving compliance.
What is a Targeted Risk Analysis (TRA) in PCI DSS v4.0?
So, what is a TRA, really? It’s not just ticking boxes on a checklist. A Targeted Risk Analysis is a focused, laser-precise evaluation of the risks specific to your environment. It’s about understanding the unique security needs of your organization. You can use TRA to implement PCI DSS v4.0. TRAs are more than just a general risk assessment that casts a wide net; instead, it’s a direct hit on PCI DSS requirements that demand a tailored approach. It’s about effectively managing threats and vulnerabilities that are relevant to your specific operations.
Fundamentally, a TRA answers crucial questions: How often should a particular activity be performed, and how effectively should it be performed to maintain a secure posture and stay compliant? Think of it like this: TRAs allow organizations to move away from a ‘one-size-fits-all’ approach. As I’ve learned throughout my career, one size often fits no one perfectly. TRAs allow organizations to optimize their security practices based on real risk, allocating resources effectively to provide the most effective data protection. This enhanced flexibility and security are invaluable for any security operations team.
Why are TRAs Important for PCI DSS v4.0?
PCI DSS v4.0 places an increased emphasis on a risk-based approach. This isn’t just a trend; it’s a necessity reflecting the evolving threat landscape and encouraging organizations to be more proactive and strategic with their security efforts. The Verizon 2024 Data Breach Investigations Report continuously shows that attackers often exploit known vulnerabilities. You can use TRAs to focus your limited resources on what matters most, so you’ll be able to quickly shut down the vulnerabilities.
Specifically, TRAs enable your organization to:
-
Prioritize Resources: TRAs ensure efficient resource allocation. Organizations can focus on the most critical threats to protect their cardholder data, rather than applying a blanket security strategy.
-
Gain Flexibility: Unlike prescriptive measures, TRAs allow you to customize controls based on a thorough risk assessment, ensuring they align perfectly with your organization’s processes.
-
Improve Security Posture: By analyzing risk and adapting accordingly, TRAs enhance your overall security, reduce vulnerabilities, and improve protection against cyberattacks.
Key Requirements for TRAs in PCI DSS v4.0
PCI DSS v4.0 requirements are comprehensive, and TRAs demand meticulous attention. Here’s a simplified overview of the key requirements calling for a TRA:
-
Requirement 12.3.1: “Perform a Targeted Risk Analysis (TRA). Confirm the review frequency is appropriate to the Entity and its environment.” TRAs should be carried out to ensure that the frequency of PCI DSS activities is aligned with the assessment.
-
Requirement 12.3.2: “For each customized approach, document how the control has been customized to implement a protection that is above and beyond that stated in the specific approach and demonstrate how controls mitigate risks.” You need to show that your implemented controls truly mitigate risk.
Remember, performing Targeted Risk Analysis is more than a mere formality; it empowers you to implement enhanced protection for your cardholder data and maintain a more effective security posture. One effective approach is utilizing the “3-5-2” control framework. This handles controls better. It involves three controls: preventative, detective, and corrective. They protect the CDE.
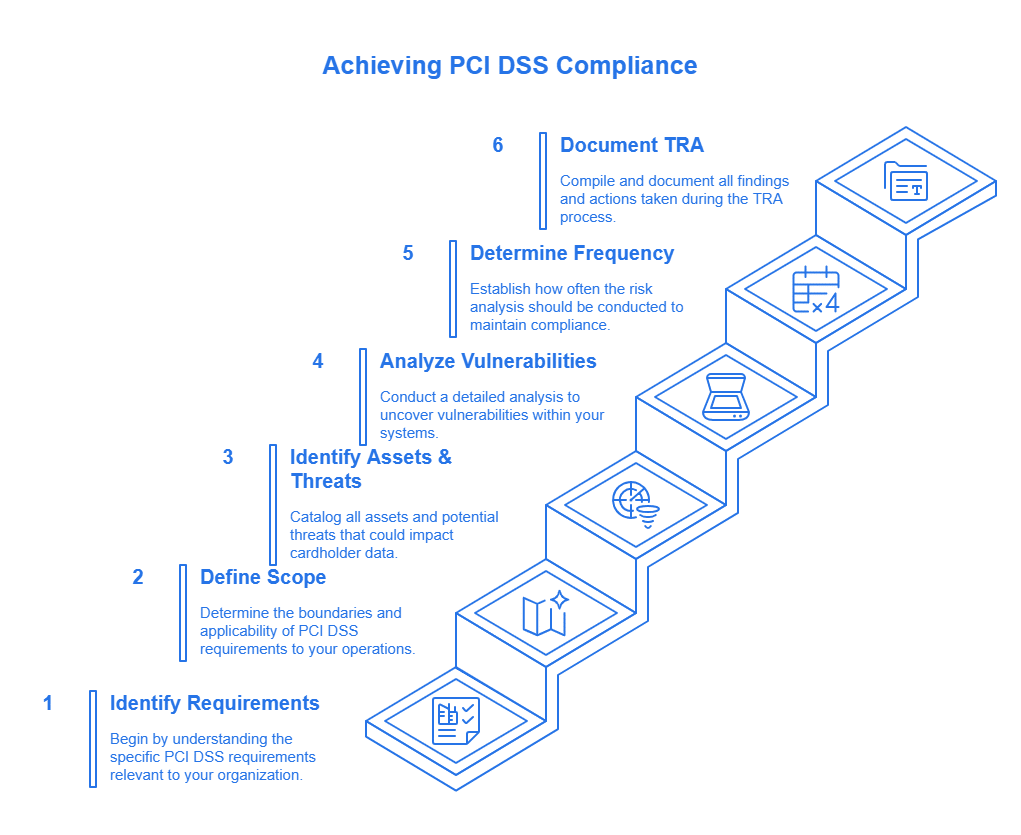
Steps to Conduct a Successful Targeted Risk Analysis
So, what actionable steps can you take right now to implement Targeted Risk Analysis and meet PCI DSS v4.0 compliance?
-
Identify PCI DSS Requirements Requiring TRAs: Scrutinize PCI DSS v4.0 and identify all requirements explicitly calling for a TRA. Go the PCI Security Standards Council (SSC) website. and download your PCI DSS v4.0.
-
Define the Scope: Determine which processes and systems the regulation will apply to. Outline the scope and impact of the analysis, ensuring you analyze relevant data flows and allocate your resources efficiently.
-
Identify Assets and Threats: You must first identify critical assets within the in-scope systems. After that, look at potential threats and how they may affect your environment. Make sure you have up-to-date and comprehensive plans for the top security threats, allowing your team to always be prepared.
-
Analyze Vulnerabilities: Evaluate the likelihood of each vulnerability being exploited. Implement steps necessary to avoid future incidents. Using vulnerability scanning tools will enable you to detect any emerging issues.
-
Determine TRA Frequency: Conduct a risk review and outline the frequency of these scans. Proper planning and prioritization help allocate resources efficiently.
-
Document and Maintain: Document the TRA process, record findings, and explain how risk affects the security controls. Review and maintain your TRA, adapting it to any changes to your environment. Consider storing the TRA to ensure consistency and accuracy in your efforts.
Digging Deeper: Key Considerations for Each Stage
Let’s elaborate on a few of the key steps and highlight the finer details of the PCI DSS.
Identifying Requirements:
-
Focus on Customized Approaches: TRAs are most critical when using customized controls. Document how the tailored controls meet the intent and rigor of PCI DSS standards, often requiring going above and beyond the requirements of the PCI DSS regulations.
-
Leverage PCI SSC Resources: Use the resources provided by the PCI Security Standards Council to accurately interpret and apply the PCI DSS requirements.
Defining Scope:
-
Document Data Flows: Create accurate and up-to-date diagrams that illustrate all cardholder data flows, showing what your security operations team is responsible for and the scope of that task.
-
Review Network Segmentation: Verify and refine network segmentation to minimize the scope of your PCI DSS assessment, reduce the risk of data breaches, and segregate sensitive data.
Identifying Assets and Threats:
-
Maintain Asset Inventory: Ensure all systems handling cardholder data are inventoried and appropriately secured.
-
Use Threat Modeling: Proactively identify potential threat vectors by using threat modeling to anticipate attack scenarios.
Analyzing Vulnerabilities:
-
Prioritize Vulnerabilities: Scan your infrastructure, look for high-value targets, and prioritize remediation. This helps security operations teams stay efficient and protect the CDE.
-
Implement Remediation Plans: Create remediation plans with clear steps and timelines, ensuring controls are in place for any identified vulnerabilities.
Determine TRA Frequency:
-
Consider Business Impact: Make sure your assessments are aligned with business operations, ensuring minimal disruption. Keep the frequency appropriate.
-
Adjust Based on Findings: Use a dynamic method. Your frequency will change based on findings. Prevent issues from lingering.
Documentation and Maintenance:
-
Use Risk Registers: Use risk registers to log each component of your analysis. Ensure proper tracking.
-
Review Controls Regularly: Continuously monitor and update your controls. Keep them aligned with key changes to your IT systems.
Best Practices for Implementing and Performing TRAs
Ensure effective protection. Below is a summary of practices.
-
Prioritize Documentation: Maintain detailed records, including your TRA procedures, results, and decisions. This comprehensive record allows a streamlined assessment process. Ensure that future efforts are accurate. They also need to be consistent with security standards.
-
Integrate Threat Intelligence: Incorporate the latest threat intelligence from reputable sources to stay up-to-date with emerging threats and respond dynamically to evolving tactics and techniques. This proactive approach enables your security operations team to stay one step ahead of malicious actors. Reduce the risk of falling victim to a previously unseen vulnerability.
-
Engage Key Stakeholders: Involve key stakeholders across departments, including IT, Security, Compliance, and Legal. This collaborative approach fosters understanding of the risks. Ensure that security strategies align with business goals. They also need to align with operational realities.
-
Leverage Automation: Automating tasks can streamline operations. It can improve efficiency of TRAs. By using automation, organizations are better equipped. Rapidly respond to security threats. Adapt quickly.
Common Challenges and How to Overcome Them
Implementing TRAs can be complex. Here are challenges and solutions:
-
Lack of Expertise: If your staff lacks skills, consider reaching PCI DSS experts or QSAs.
-
Keeping Up with Changes: Technology and threat landscapes change constantly. Be adaptable. Review your TRAs often. Keep up with dynamic changes.
-
Integration Difficulties: Resolve this by integrating TRAs into your system lifecycle. Create a holistic security posture. Protect your CDE.
Let Compliance Labs provide the expertise, resources, and support. Ensure you stay compliant and secure. We offer training programs and expert consultations. Help your internal teams build skills.
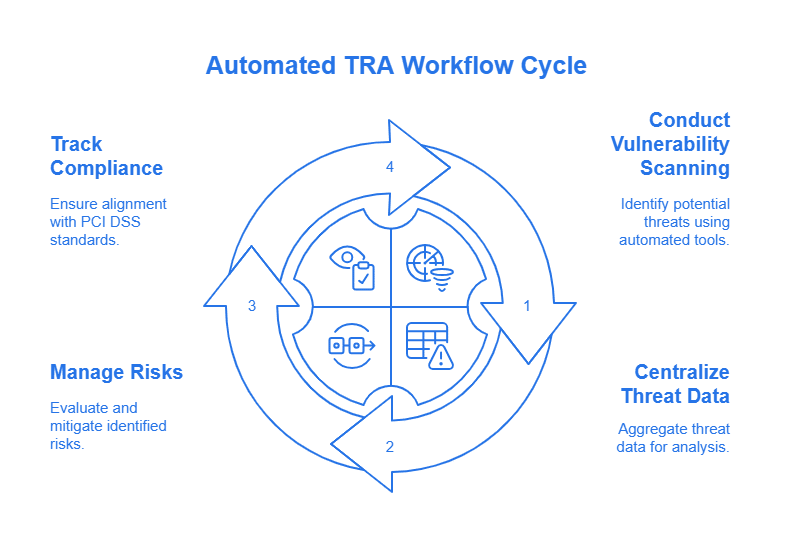
The Role of Technology and Automation
Leveraging the correct technology is crucial. Automation will be important for efficiently managing Targeted Risk Analyses. This may include:
-
Vulnerability Scanning Tools: Automate threat detection. Assist security analysts to perform operations more effectively. Identify and prioritize risk factors.
-
Security Information and Event Management (SIEM) Solutions: Centralize security information. Manage incident operations. Security teams have a clear view of security. SIEM systems can aggregate information. Analysts use this information for their reports.
-
Risk Management Platforms: Streamline your risk analysis. Manage compliance. Use an integrated platform. This will help your team more effectively manage your TRA.
You can integrate these tools. Create a holistic, automated approach. Allow for efficient tracking.
Future-Proofing Your PCI DSS Compliance
You must take a proactive strategy. Evolve to stay compliant. With a dynamic approach, you’re able to better respond. You need to respond to all of your organization’s needs. Ensure that you are not susceptible to new attacks. By continuously adapting, your security operations team will be prepared. Be prepared for any new issues that may arise.
Staying compliant also includes investing in staff training. Your personnel are always up-to-date with regulations. You can engage with partners. Keep your PCI DSS requirements at the cutting edge. Moreover, using AI capabilities will streamline the process.
Conclusion:
Targeted Risk Analyses are now vital. Organizations seek to maintain PCI DSS v4.0 compliance. They also need to maintain robust security operations. Take these steps. Follow our best practices outlined above. Mitigate risks effectively. Protect cardholder data. Foster a culture of cybersecurity awareness. Promote diligence.
Remember, compliance is more than a checkbox. It’s a continuous process. It is a strategic process that can bring tangible business benefits.