As cyber threats become increasingly pervasive and sophisticated, the need for robust cybersecurity measures has never been more crucial. Organizations must prioritize their security stance to protect sensitive data and maintain trust among stakeholders, clients, and partners. One pivotal framework guiding this endeavor is the NIST Cybersecurity Framework (CSF), which assists organizations in assessing and enhancing their cybersecurity posture. Adhering to NIST CSF not only bolsters security but also demonstrates a commitment to responsible information management. In this article, we will explore the NIST CSF, the significance of cybersecurity posture evaluations, and present key questions to help you gauge your organization’s alignment with these standards.
Understanding the NIST CSF and Cybersecurity Posture
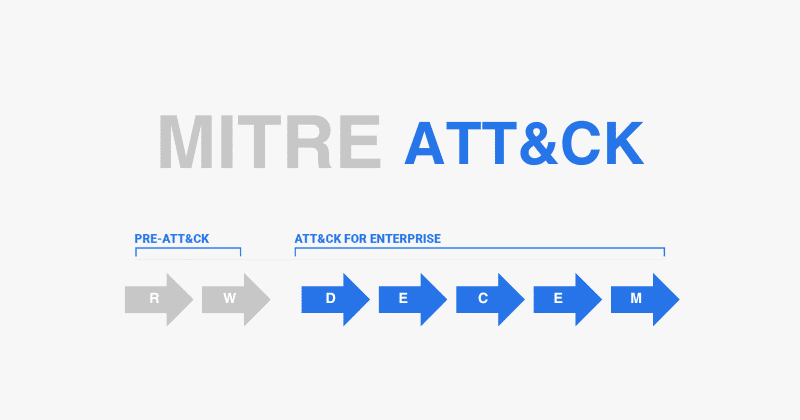
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework represents a set of guidelines aimed at establishing a robust cybersecurity posture across private sector organizations. Developed by the National Institute of Standards and Technology (NIST) through collaboration with industry experts, the framework offers a pragmatic and cost-effective strategy to manage cybersecurity risks at all organizational levels. Its foundation rests on five core functions: Identify, Protect, Detect, Respond, and Recover, each constituting essential components of comprehensive cybersecurity management.
- Identify: This foundational element involves a thorough understanding of the organization’s environment, focusing on assets, vulnerabilities, and pertinent regulatory requirements to inform effective risk management strategies.
- Protect: This function emphasizes the implementation of appropriate safeguards to limit or contain the impact of potential cybersecurity incidents.
- Detect: Timely detection of cybersecurity events is crucial for an organization to recognize and respond to incidents promptly.
- Respond: This entails developing a structured response to any detected cybersecurity incident, ensuring swift action to mitigate damage.
- Recover: Focused on restoring capabilities and services post-incident, this function ensures organizations can quickly bounce back from disruptions.
Why Evaluate Your Cybersecurity Posture?
Continual evaluation of your cybersecurity posture is imperative for identifying vulnerabilities and enhancing resilience against potential attacks. By systematically assessing security frameworks, organizations can expose gaps in their defenses, prioritize risks, and confirm their readiness in the face of evolving cyber threats. Cybersecurity posture assessment is not simply a box-ticking exercise; it demands an ongoing commitment to risk understanding and mitigation, fostering a culture dedicated to continuous improvement. Regular evaluations also enable organizations to recalibrate their cybersecurity strategies in response to the dynamic threat landscape.
Key Questions for Assessing Alignment with the NIST Cybersecurity Framework
1. Do You Understand Your Cybersecurity Risks?
Having a current understanding of your specific cybersecurity risks is vital. This process entails identifying potential threats and evaluating their potential impacts on your operations. Risk assessments should be routine, integrating insights from various departments for a holistic view of vulnerabilities.
2. Is There a Defined Cybersecurity Governance Structure?
A strong governance structure is crucial for effective cybersecurity management. This includes defining roles and responsibilities, establishing measurable objectives, and ensuring alignment with organizational goals. A well-structured governance framework promotes accountability and streamlined communication.
3. Are Cybersecurity Policies Regularly Updated?
Given the rapid evolution of cybersecurity threats, it is essential to maintain robust policies that reflect current best practices. Regular revisions ensure policies remain relevant and enforceable. Senior leadership should consistently review and update policies, adapting insights from assessments, new technologies, and legislative changes.
4. Have You Identified and Prioritized Your Assets?
Understanding which assets require protection is a pivotal step in effective risk management. Organizations must identify their valuable data, software, and hardware, prioritizing them accordingly. By grasping the significance of each asset, organizations can implement appropriate protective measures based on sensitivity and value, utilizing bullet points to clearly list assets and their priorities.
5. Is There a Risk Communication Plan in Place?
Effective communication surrounding cybersecurity risks is critical at all levels of an organization. Implementing a risk communication plan ensures that employees recognize potential threats and their roles in mitigation strategies. This plan should detail information dissemination strategies, employee training, and incident reporting processes.
6. Are Access Controls Effectively Managed?
Robust management of access controls is fundamental to protecting sensitive information. Organizations should conduct thorough assessments to ensure that only authorized personnel access critical systems and data.
7. Do You Conduct Regular Vulnerability Assessments?
Frequent vulnerability assessments are essential for identifying and addressing weaknesses within an organization’s defenses. These evaluations should utilize methodologies, including penetration testing and threat modeling, to discover vulnerabilities before they can be exploited. Documenting outcomes enhances overall security posture over time, increasing organizational responsiveness to threats.
8. Is Incident Response Preparedness in Place?
A well-defined incident response plan is crucial for minimizing the consequences of a cybersecurity incident. Organizations should establish clear protocols outlining steps to take following a breach. Regular drills can prepare teams for real-life scenarios, enhancing their ability to respond promptly and effectively to incidents.
9. Are Continuous Monitoring and Improvement Practices Implemented?
Ongoing monitoring of the cybersecurity environment is essential. This involves tracking systems for suspicious activity, continually reviewing security measures, and adapting defenses in response to new threats.
10. Do You Educate and Train Employees on Cybersecurity?
Employees are often the first line of defense against cyber threats. Regular training ensures they identify potential threats and understand their roles in protecting organizational assets. Real-life scenario-based training programs can significantly engage and inform staff members.
Building a Strategy for Compliance with NIST Cybersecurity Framework
Establishing a Cybersecurity Action Plan
Creating a dynamic cybersecurity action plan necessitates clear objectives, resource allocation, and defined responsibilities for NIST CSF adherence. This plan should include timelines and accountability measures for ongoing evaluation, allowing organizations to measure their progress efficiently.
Emphasizing Risk Management and Culture
Fostering a cybersecurity-conscious culture within your organization is essential for effective risk management. By embedding cybersecurity considerations into all business operations, organizations encourage open dialogue about potential risks.
Utilizing Resources for Compliance
Numerous resources are available for organizations seeking to comply with NIST CSF. Leveraging tools and guidance provided by NIST and other reputable frameworks significantly enhances security posture. Engaging compliance software vendors can streamline assessment and reporting processes.
Conclusion
Aligning with NIST CSF standards is integral to bolstering your organization’s cybersecurity posture. By consistently evaluating cybersecurity practices through the lens of the key questions outlined in this article, organizations can identify gaps and strengthen defenses against potential threats. Remember, cybersecurity is not a one-time task but a persistent commitment to safeguarding valuable data. Now is the time to act—implement these questions and develop a comprehensive cybersecurity strategy that aligns with NIST CSF standards to protect your organization’s invaluable assets. Prioritizing cybersecurity and cultivating a culture of vigilance will enable your organization to flourish in today’s increasingly digital environment.